-
People View all
Verified account@SecNielsen Sixth Secretary of
@DHSgov. Florida Native.@UVALaw &@Georgetown grad. Working to protect and secure our homeland.Verified account@PressSec @WhiteHouse Press Secretary. Proudly representing@POTUS Trump's Administration. Tweets may be archived: http://wh.gov/privacy . -
President Muhammadu Buhari in Borno State, attends the 2018 Nigerian Army Day Celebration in Monguno.
#Security pic.twitter.com/nMxgHgYp4t



-
Women’s economic empowerment is a critical tool for their access to leadership & decision-making positions. I encourage them to take part in all
#political,#peace,#security and#development processes that will sustain their communities. Read: https://news.un.org/en/story/2018/07/1014002 …pic.twitter.com/aFfP3GHTih



-
I'll be giving a talk about
#WomenInTech to some high schoolers and their teachers. I want to tell them about the amazing work being done by Women in Tech (and#Security). Who would you recommend I tell them about? -
#security#academictwitter does anyone know of any work on causal modeling of security incidents (e.g., bayesian models of what caused the incident)? pointers requested, please :)Show this thread -
So called
#Indian#Security forces, or better known as#terrorist and#occupation forces, interrogate and torture a#kashmiri civilian.#Kashmir, not#Syria or#Palestine.#WarCrimes#Genocide#EthnicCleansing#CrimesAgainstHumanitypic.twitter.com/9OxbpHjrL7 -
-
#Syscoin#Update: "Debrief on Recent Syscoin Trading Activity": http://j.mp/2zbgBMb$SYS#SAFU#Security#Binance#Altcoins#Cryptocurrencies#Fintech#Wiki#Ecommercepic.twitter.com/7jk1ICfIho

-
The Rise of
#Robotics and#AI:#tech#MachineLearning#BigData#makeyourownlane#IoT#VR#DataScience#blockchain#ArtificialIntelligence#robots#robot#technology#infosec#security#gdpr#data#infographic#DataAnalytics#ML ht:@mikequindazzi#BigData#MachineLearning#AI#IoTpic.twitter.com/qp6rnwCaRU
-
What are some use-cases for Internet of Things?
#IoT#SmartCity#CyberSecurity#Healthcare#sensors#Security#IIoT#infosec#AI#ML#LiDAR#startups#innovation MT@Fisher85Mpic.twitter.com/FmwMPoYJHQ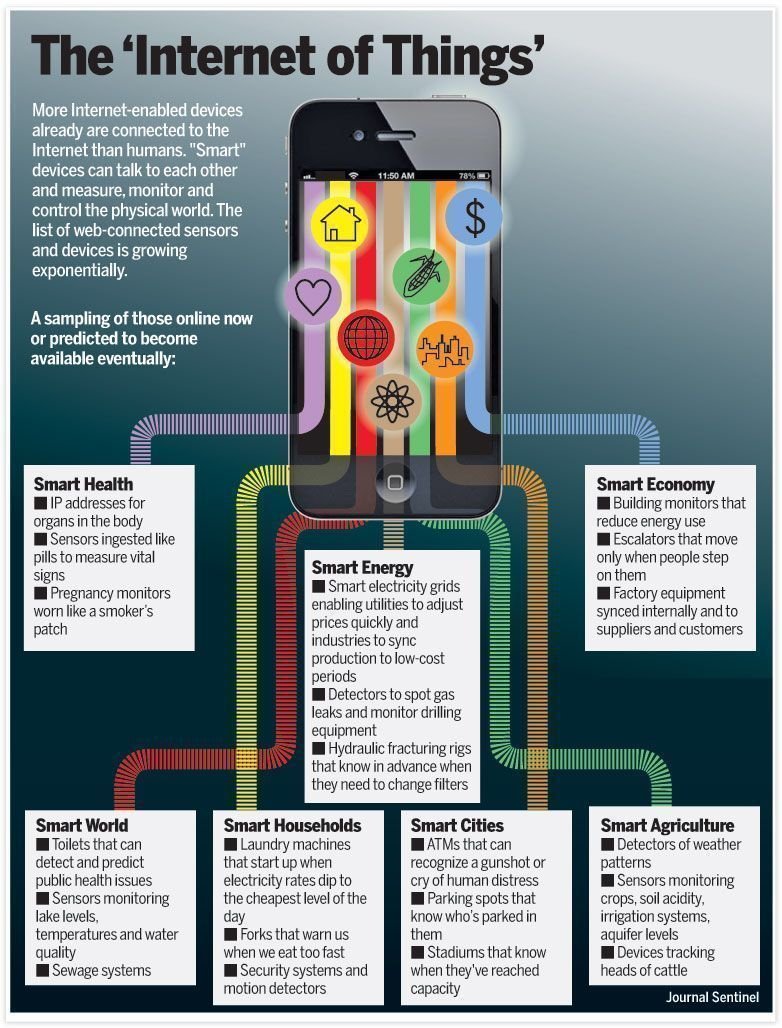
-
10 things will become obsolete. Thanks to the
#IoT#IIoT#Blockchain#BigData#Analytics#AI#IoE#DataScience#Robotics#Innovation#Startups#M2M#MachineLearning#Security#Medical#Industry#MobileDevicespic.twitter.com/RAv6bT1ObC
-
Violent episodes involving
#militant#Islamist groups in#Africa in 2017. Under-reported outside of Africa (as usual).#Conflict#security#Development#war#BokoHaram#AlShabaab#ISIS#Terrorists#Maps#map#CivilWar#terrorism#maps#mappic.twitter.com/UTlowA29LK
-
6 Key Requirements for
#IoT Success {Infographic}#CyberSecurity#BigData#Analytics#Sensors#DigitalTransformation#dataviz#Security#SMM@Datawatchpic.twitter.com/LCPdma4T6l
-
Please share this work and training opportunity with anyone who lives in Royal Borough of Kensington & Chelsea, City of Westminster, Hammersmith & Fulham or Brent in London
 Thank you
Thank you 
#nottinghillcarnival#freetraining#workopportunity#stewarding#security pic.twitter.com/eDyrRPSD9z

-
“Black Box has worked for my family for almost 30 years protecting our home & businesses. They are true professionals and I have complete confidence in their service which is testament to the longevity of our relationship.” Jonathan Smith
@kingsleyfinance#excellence#Security -
The clocks on the
#Nexus network nodes maintain the same exact time, within 1 sec of each other, thus preventing a 'time gap' attack vector.#UnifiedTime#Security#51attack -
Just had a very good meeting with my great friend Ambassador Fatima Khamis Al Mazrouie from
@UAEEmbassyDK . We discussed common goals and priorities including#Iran and the terrible situation in#Yemen.#security
 pic.twitter.com/JQnrrs6niR
pic.twitter.com/JQnrrs6niR
-
Here are some useful tips to privacy-proof your desk at work
#security#privacy#infosec#tips#SheSecures#hacked#cybersecuritypic.twitter.com/QEv2A5BB67
-
Validation of Red Hat's stance on security. "Open source library vulnerabilities increased by 53.8% in 2016, while Red Hat Linux vulnerabilities have decreased."
#security@RedHat@RedHatGovhttps://www.linux.com/blog/2018/7/decreasing-vulnerabilities-seen-red-hat-linux …
Loading seems to be taking a while.
Twitter may be over capacity or experiencing a momentary hiccup. Try again or visit Twitter Status for more information.



 Just Follow & Retweet to Enter - Will announce winner on Saturday 7th 12:00 UTC
And remember - Keep your coins safe and cold!
Just Follow & Retweet to Enter - Will announce winner on Saturday 7th 12:00 UTC
And remember - Keep your coins safe and cold!




















